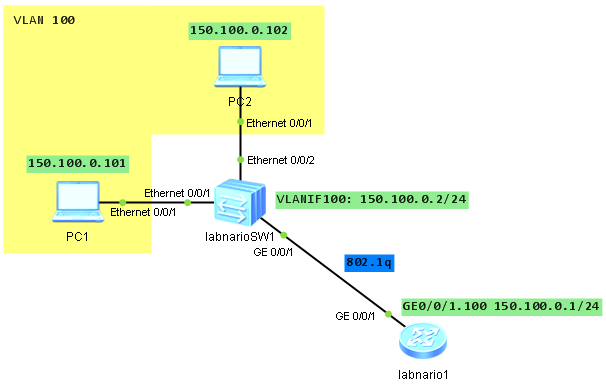
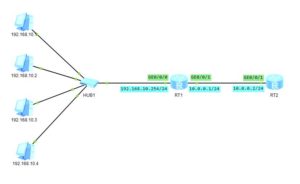
You, as the network administrator, were tasked with providing access to a network, where 4 machines have been connected.
It is simple task. Nothing can happen, but…
Everything is ready and you are checking connectivity between RT2 and those machines, and… To your suprise, you can only ping even-numbered IP addresses:
[RT2]ping 192.168.10.1
PING 192.168.10.1: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
[RT2]ping 192.168.10.2
PING 192.168.10.2: 56 data bytes, press CTRL_C to break
Reply from 192.168.10.2: bytes=56 Sequence=1 ttl=127 time=30 ms
Reply from 192.168.10.2: bytes=56 Sequence=2 ttl=127 time=20 ms
Reply from 192.168.10.2: bytes=56 Sequence=3 ttl=127 time=30 ms
Reply from 192.168.10.2: bytes=56 Sequence=4 ttl=127 time=40 ms
Reply from 192.168.10.2: bytes=56 Sequence=5 ttl=127 time=30 ms
[RT2]ping 192.168.10.3
PING 192.168.10.3: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
[RT2]ping 192.168.10.4
PING 192.168.10.4: 56 data bytes, press CTRL_C to break
Reply from 192.168.10.4: bytes=56 Sequence=1 ttl=127 time=30 ms
Reply from 192.168.10.4: bytes=56 Sequence=2 ttl=127 time=40 ms
Reply from 192.168.10.4: bytes=56 Sequence=3 ttl=127 time=30 ms
Reply from 192.168.10.4: bytes=56 Sequence=4 ttl=127 time=30 ms
Reply from 192.168.10.4: bytes=56 Sequence=5 ttl=127 time=30 ms
What has happend?
You are sure that IP addresses and GW of PCs are correct. Let’s look into configuration of RT1 and RT2:
[RT2]
#
interface GigabitEthernet0/0/1
ip address 10.0.0.2 255.255.255.0
#
ip route-static 192.168.10.0 255.255.255.0 10.0.0.1
[RT1]
#
interface GigabitEthernet0/0/0
ip address 192.168.10.254 255.255.255.0
traffic-filter inbound acl 3000
#
interface GigabitEthernet0/0/1
ip address 10.0.0.1 255.255.255.0
Everything seems to be OK. The only thing we should check is the access list number 3000. So let’s get to the ACL:
[RT1]display acl 3000
Advanced ACL 3000, 2 rules
Acl's step is 5
rule 10 permit ip source 192.168.10.0 0.0.0.254 (20 matches)
rule 15 deny ip (20 matches)
And we have a reason for the problem.
What is happening here? Let’s try to compare the IP address and the wildcard mask. Write them in binary:
11000000.10101000.00001010.00000000
00000000.00000000.00000000.11111110
We don’t care about the first 3 octects, as the bit in wildcard mask is 0. We have to focus on the last octet.
In our access list, the first seven bits of the last octet are all 1s. It means that the seven bits can be anything. The final bit in the last octet of our wildcard mask is 0. So, the very last bit in any IP address coming into this interface always has to be zero. The rest of the bits in that final octet can be anything.
What does this mean in practice?
It means that we can ping only IP addresses with the last bit 0. So we can only ping even-numbered IP addresses.
What if you want to ping only odd-numbered IP addresses. Nothing easier, just start the IP address in ACL at an odd number :
#
acl number 3000
rule 10 permit ip source 192.168.10.1 0.0.0.254
rule 15 deny ip
#
Anyway, can you imagine the following wildcard mask: 0.0.255.0? What would happen if you used it with 10.10.0.1/24 IP address?
Finally you could have access to 10.10.0.1, 10.10.1.1, 10.10.2.1 and so on. How to use it in practice?
Assume that you use 10.10.0.0/16 subnet accross you entire network. You can split it to many /24 subnets. On each subnet there is a machine with the IP address 10.10.x.100 which is acting as a server offering the same functionality on each subnet. So you want to have access only to those machines, I mean 10.10.0.100, 10.10.1.100, 10.10.2.100…
To achive this goal, just configure the ACL like below:
#
acl number 3000
rule 10 permit ip source 10.10.0.100 0.0.255.0
rule 15 deny ip
#
This article shows how powerful the wildcard mask can be. You can actually do interesting stuff with it, can’t you?
The post fun with wildcard mask on Huawei device appeared first on Labnario.